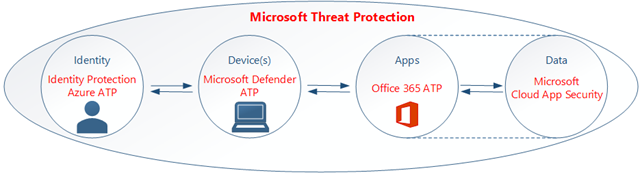
This telemetry is made up of signals from across Microsoft’s services such as Microsoft Defender ATP, Office 365 ATP and data from Microsoft’s cybersecurity teams and global law enforcement etc. Microsoft call this pool of data the ‘Microsoft Intelligent Security Graph’. Microsoft runs world-class machine learning, AI and big data. Microsoft Defender for Office 365 (or Office 365 Advanced Threat Protection if you're old fashioned) is an amazing toolset for securing your Office 365 environment with some extremely powerful features. Previously, I have written about the built in Preset Security Policies that Microsoft have recently made available. Defender for Office 365 is Microsoft's cloud-based service that protects against phishing, spoofing, and other sophisticated malware attacks through malicious links delivered through email and Office collaboration tools. 365, including SharePoint Online, OneDrive for Business, and Microsoft Teams. Microsoft Defender for Endpoint is a holistic, cloud delivered endpoint security solution that includes risk-based vulnerability management and assessment, attack surface reduction, behavioral based and cloud-powered next generation protection, endpoint detection and response (EDR), automatic investigation and remediation, managed hunting services, rich APIs, and unified security management.
-->Learn about the robust security solutions in Defender for Office 365 to better protect your email and collaboration tools.
Defender for Office 365 & Exchange Online Protection
Overview
Getting started with Defender for Office 365
Get Started
Evaluate Defender for Office 365
How-To Guide
Setting up Email Authentication protection
How-To Guide
Set up Exchange Online Protection
Overview
Prevent

Overview
Detect
Overview
Investigate
Overview
Investigate in EOP
Overview
Respond
Overview

Automate
Overview
-->Important
The improved Microsoft 365 security center is now available. This new experience brings Defender for Endpoint, Defender for Office 365, Microsoft 365 Defender, and more into the Microsoft 365 security center. Learn what's new.
Applies to
Important
This article is intended for business customers who have Microsoft Defender for Office 365. If you are using Outlook.com, Microsoft 365 Family, or Microsoft 365 Personal, and you're looking for information about Safe Links or Safe Attachments in Outlook, see Advanced Outlook.com security for Microsoft 365 subscribers.
Microsoft Defender for Office 365 safeguards your organization against malicious threats posed by email messages, links (URLs), and collaboration tools. Defender for Office 365 includes:
Threat protection policies: Define threat-protection policies to set the appropriate level of protection for your organization.
Reports: View real-time reports to monitor Defender for Office 365 performance in your organization.
Threat investigation and response capabilities: Use leading-edge tools to investigate, understand, simulate, and prevent threats.
Automated investigation and response capabilities: Save time and effort investigating and mitigating threats.
Interactive guide to Microsoft Defender for Office 365
In this interactive guide you'll learn how to safeguard your organization with Microsoft Defender for Office 365. You'll see how Defender for Office 365 can help you define protection policies, analyze threats to your organization, and respond to attacks.
Getting Started
If you're new to Microsoft Defender for Office 365 or learn best by doing, you may benefit from breaking initial Defender for Office 365 configuration into chunks, investigating, and viewing reports using this article as a reference. Here are logical early configuration chunks:
- Configure everything with 'anti' in the name.
- anti-malware
- anti-phishing
- anti-spam
- Set up everything with 'safe' in the name.
- Safe Links
- Safe Attachments
- Defend the workloads (ex. SharePoint Online, OneDrive, and Teams)
- Protect with Zero-Hour auto purge
To learn by doing, click this link.
Note
Microsoft Defender for Office 365 comes in two different Plan types. You can tell if you have Plan 1 if you have 'Real-time Detections', and Plan 2, if you have Threat Explorer. The Plan you have influences the tools you will see, so be certain that you're aware of your Plan as you learn.
Microsoft Defender for Office 365 Plan 1 and Plan 2
The following table summarizes what's included in each plan.
| Microsoft Defender for Office 365 Plan 1 | Microsoft Defender for Office 365 Plan 2 |
|---|---|
| Configuration, protection, and detection capabilities: | Microsoft Defender for Office 365 Plan 1 capabilities --- plus --- Automation, investigation, remediation, and education capabilities: |
Microsoft Defender for Office 365 Plan 2 is included in Office 365 E5, Office 365 A5, Microsoft 365 E5 Security, and Microsoft 365 E5.
Microsoft Defender for Office 365 Plan 1 is included in Microsoft 365 Business Premium.
Microsoft Defender for Office 365 Plan 1 and Microsoft Defender for Office 365 Plan 2 are each available as an add-on for certain subscriptions. To learn more, see Feature availability across Microsoft Defender for Office 365 plans.
The Safe Documents feature is only available to users with the Microsoft 365 E5 or Microsoft 365 E5 Security licenses (not included in Microsoft Defender for Office 365 plans).
If your current subscription does not include Microsoft Defender for Office 365, contact sales to start a trial, and see how Defender for Office 365 can work for your organization.
Configure Microsoft Defender for Office 365 policies
What Is Microsoft Defender For Office 365
With Microsoft Defender for Office 365, your organization's security team can configure protection by defining policies in the Security & Compliance Center (Go to https://protection.office.com > Threat management > Policy.)
Learn more by watching this video.
Tip
For a quick list of policies to define, see Protect against threats.
Defender for Office 365 Policies
The policies that are defined for your organization determine the behavior and protection level for predefined threats. Policy options are extremely flexible. For example, your organization's security team can set fine-grained threat protection at the user, organization, recipient, and domain level. It is important to review your policies regularly because new threats and challenges emerge daily.
Safe Attachments: Provides zero-day protection to safeguard your messaging system, by checking email attachments for malicious content. It routes all messages and attachments that do not have a virus/malware signature to a special environment, and then uses machine learning and analysis techniques to detect malicious intent. If no suspicious activity is found, the message is forwarded to the mailbox. To learn more, see Set up Safe Attachments policies.
Safe Links: Provides time-of-click verification of URLs, for example, in emails messages and Office files. Protection is ongoing and applies across your messaging and Office environment. Links are scanned for each click: safe links remain accessible and malicious links are dynamically blocked. To learn more, see Set up Safe Links policies.
Safe Attachments for SharePoint, OneDrive, and Microsoft Teams: Protects your organization when users collaborate and share files, by identifying and blocking malicious files in team sites and document libraries. To learn more, see Turn on Defender for Office 365 for SharePoint, OneDrive, and Microsoft Teams.
Anti-phishing protection in Defender for Office 365: Detects attempts to impersonate your users and internal or custom domains. It applies machine learning models and advanced impersonation-detection algorithms to avert phishing attacks. To learn more, see Configure anti-phishing policies in Microsoft Defender for Office 365.
View Microsoft Defender for Office 365 reports
Microsoft Defender for Office 365 includes an advanced reporting dashboard to monitor your Defender for Office 365 performance. You can access it at Reports > Dashboard in the Security & Compliance Center.
Reports update in real-time, providing you with the latest insights. These reports also provide recommendations and alert you to imminent threats. Predefined reports include the following:
... and several more.
Use threat investigation and response capabilities
Microsoft Defender for Office 365 Plan 2 includes best-of-class threat investigation and response tools that enable your organization's security team to anticipate, understand, and prevent malicious attacks.
Threat trackers provide the latest intelligence on prevailing cybersecurity issues. For example, you can view information about the latest malware, and take countermeasures before it becomes an actual threat to your organization. Available trackers include Noteworthy trackers, Trending trackers, Tracked queries, and Saved queries.
Threat Explorer (or real-time detections) (also referred to as Explorer) is a real-time report that allows you to identify and analyze recent threats. You can configure Explorer to show data for custom periods.
Attack Simulator allows you to run realistic attack scenarios in your organization to identify vulnerabilities. Simulations of current types of attacks are available, including spear phishing credential harvest and attachment attacks, and password spray and brute force password attacks.
Save time with automated investigation and response

(NEW!) When you are investigating a potential cyberattack, time is of the essence. The sooner you can identify and mitigate threats, the better off your organization will be. Automated investigation and response (AIR) capabilities include a set of security playbooks that can be launched automatically, such as when an alert is triggered, or manually, such as from a view in Explorer. AIR can save your security operations team time and effort in mitigating threats effectively and efficiently. To learn more, see AIR in Office 365.
Permissions required to use Microsoft Defender for Office 365 features
To access Microsoft Defender for Office 365 features in the Security & Compliance Center, you must be assigned an appropriate role. The following table includes some examples:
| Role or role group | Resources to learn more |
|---|---|
| global administrator (this can be assigned in either Azure Active Directory or in the Security & Compliance Center) | About Microsoft 365 admin roles |
| Security Administrator (this can be assigned in either Azure Active Directory or the Security & Compliance Center) | Administrator role permissions in Azure Active Directory |
| Exchange Online Organization Management (this is assigned in Exchange Online) | Permissions in Exchange Online |
| Search and Purge (this is assigned only in the Security & Compliance Center) | Permissions in the Security & Compliance Center |
For more information, see Permissions in the Security & Compliance Center.
Get Microsoft Defender for Office 365
Defender For Office 365 Portal
Microsoft Defender for Office 365 is included in certain subscriptions, such as Microsoft 365 E5, Office 365 E5, Office 365 A5, and Microsoft 365 Business Premium. If your subscription does not include Defender for Office 365, you can purchase Defender for Office 365 Plan 1 or Defender for Office 365 Plan 2 as an add-on to certain subscriptions. To learn more, see the following resources:
Microsoft Defender for Office 365 availability for a list of subscriptions that include Defender for Office 365 plans.
Feature availability across Microsoft Defender for Office 365 plans for a list of features included in Plan 1 and 2.
Get the right Microsoft Defender for Office 365 to compare plans and purchase Defender for Office 365.
New features in Microsoft Defender for Office 365
New features are added to Microsoft Defender for Office 365 continually. To learn more, see the following resources:
Microsoft 365 Roadmap provides a list of new features in development and rolling out.
Microsoft Defender for Office 365 Service Description describes features and availability across Defender for Office 365 plans.
See also
Defender For Office 365 Api
Automated investigation and response (AIR) in Microsoft 365 Defender1
